
The Chinese hacking group ‘Winnti’ was found using a previously undocumented malware called UNAPIMON to allow malicious processes to run without detection.
Winnti, also known as APT41, is one of the oldest (active since 2012) and most sophisticated and productive cyber espionage threats, believed to be a Chinese state actor.
They previously targeted a wide range of organizations, including governments, hardware vendors, software developers, think tanks, telecommunications service providers and educational institutions.
A new report from Trend Micro looks at the never-before-seen custom malware used in an operation they’ve been closely monitoring, attributing the cyberespionage attack to a cluster they’ve dubbed ‘Earth Freybug’.
UNAPIMON attacks
The attack begins with a malicious process inserted into the legitimate VMware Tools vmtoolsd.exe process, which executes a remote scheduled task to run a batch file that collects system information, including network configurations and user data.
Next, the second batch file (cc.bat) uses a sideloading DLL (TSMSISrv.dll) including the SessionEnv service to load UNAPIMON into memory, injecting it into the cmd.exe process.
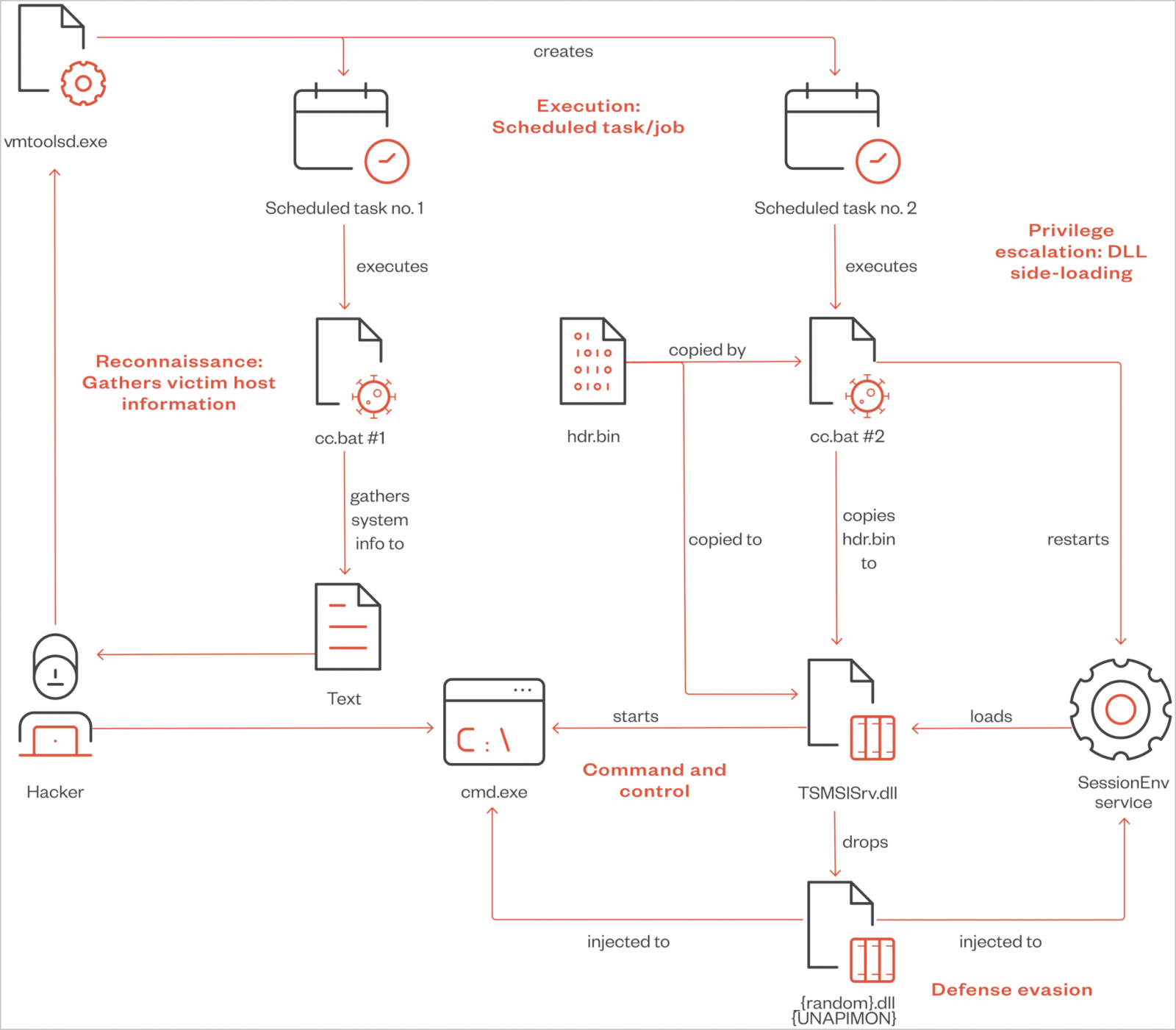
UNAPIMON is a C++ malware delivered in DLL form (_random.dll), which uses Microsoft Detours to hook the CreateProcessW API function, allowing it to unhook critical API functions in child processes.
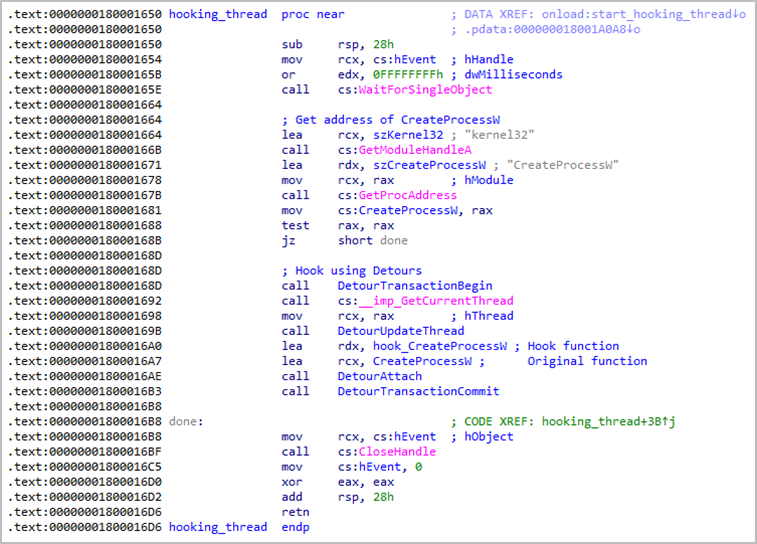
Since many security tools use API bundling to monitor malicious activity, UNAPIMON’s mechanism allows decoupling those APIs from the malicious child process to avoid detection.
According to Trend Micro’s analysis, the evasion mechanism works in different steps, as listed below:
- Connects to the ‘CreateProcessW’ API function using Microsoft Detours to intercept calls to create a process.
- Modifies the process creation call to start a new process in a suspended state, allowing manipulation before the process starts.
- It looks for specific DLLs in the suspended process, creates local copies in the %User Temp% directory, and loads those copies without resolving references to prevent errors.
- It compares the copied DLLs with the originals in the process, looking for changes in the exported addresses that indicate security software hooks.
- It copies source code over modified sections in DLLs loaded into process memory, effectively removing hooks inserted by security tools.
- It loads temporary copies of the DLL and resumes the main thread of the child process, allowing undetected execution.
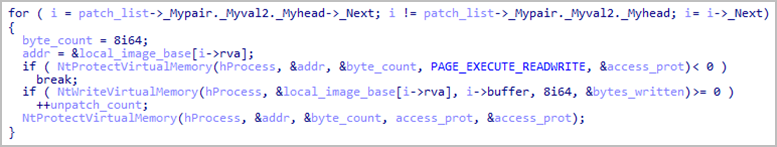
Trend Micro explains that most malware uses hooking up to intercept calls, capture sensitive data, and change software behavior. Therefore, UNAPIMON’s approach of unhooking for avoidance is an unusual technique.
“The unique and notable feature of this malware is its simplicity and originality,” Trend Micro concluded.
“Using existing technologies, such as Microsoft Detours, shows that any simple off-the-shelf library can be used maliciously if used creatively. This also demonstrated the coding skills and creativity of the malware writer.”
“In typical scenarios, it’s the malware that connects. However, in this case, it’s the opposite.”
Furthermore, using a legitimate Microsoft Detours debugger to perform the detach could allow it to avoid detecting the behavior compared to using an unknown custom routine.
Winnti hackers are known for their new methods of avoiding detection when carrying out attacks.
In 2020, hackers have been seen abusing Windows print processors to hide backdoors and remain persistent. In 2022, hackers split the Cobalt Strike beacons into 154 small pieces to avoid detection, reconstructing them into an executable only when they were ready to launch.