Security experts have recently come across a new and much more powerful version of the Vultur malware posing as the McAfee Security app on Android devices to steal your sensitive information like passwords, credit card details, photos and other files.
According to Bleeping Computer, the malware was first spotted by a fraud detection firm ThreatFabric it was distributed through the Google Play store at the end of 2022 and has been active since then. However, a new report by Fox-IT, part of the NCC Group, has revealed a new, more powerful and stealthy version of the virus.
What is Vultur and how does it work?
Scammers are sending random SMS to unsuspecting Android users saying they have detected an unauthorized transaction from their bank account and asking them to call a number to help resolve the issue.
When you call the number listed in the SMS, the scammer answers and then sends another SMS with a link asking users to download a virus-laden version of the McAfee Security application, which contains the Brunhilda malware dropper.
If you install the app, the rogue McAfee Security will then launch three payloads that allow it to use ‘Accessibility Services’ on your device, after which a connection is made to the malware’s central server.

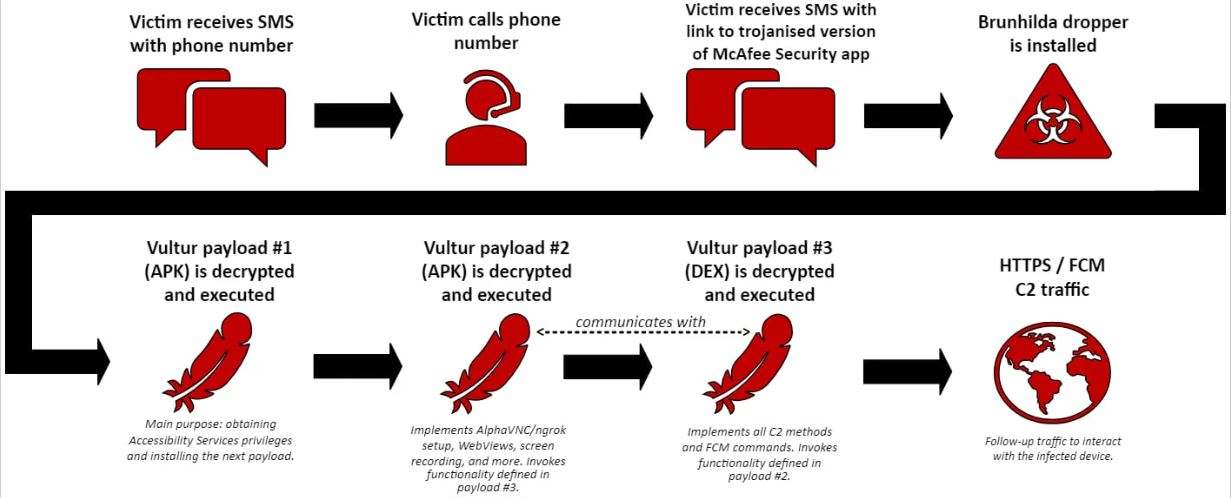 Here’s how the Vultur Trojan works. (Image source: Fox-IT)
Here’s how the Vultur Trojan works. (Image source: Fox-IT)
Once it gains access to your Android phone, Vultur will start recording everything you do on the phone, log your passwords and allow attackers to monitor and remotely take over and control your phone. As it turns out, the new version of Vultur also introduces some features like the ability to download, upload, delete, install, and find files on your phone, prevent certain apps from launching, bypass the lock screen, and even send custom notifications to trick users.
How to protect yourself from banking trojans like Vultur?
If you want to protect yourself from Vultur or other similar Android malware, do not download and install apps from URLs sent via SMS or instant messaging platforms such as WhatsApp, unless they are from a trusted source.
Another way to protect yourself is to give the app the permissions it needs for its core functionality. For example, most camera apps will only need to access your files and camera, so if they ask for access to your call logs, chances are they’re selling your data or packing some form of malware.
