
A number of iOS apps use background processes that trigger push notifications to collect user data about devices, potentially allowing the creation of fingerprint profiles used for tracking.
According to mobile researcher Mysk, which discovered the practice, these apps bypass Apple’s restrictions on background app activity and pose a privacy risk to iPhone users.
“Apps should not attempt to surreptitiously build a user profile based on collected data and may not attempt, facilitate, or encourage others to identify anonymous users or reconstruct user profiles based on data collected from APIs provided by Apple or any data that you say are collected in an ‘anonymized’, ‘aggregated’ or other non-identifiable manner,” according to the Apple App Store review guidelines section.
After analyzing the data sent by iOS background processes when receiving or deleting notifications, Mysk discovered that the practice is much more widespread than previously thought, including many apps with a significant user base.
Wake up and collect data
Apple designed iOS to not allow apps to run in the background to prevent resource consumption and improve security. When they’re not using the app, they’re suspended and eventually killed, so they can’t monitor or interfere with foreground activity.
However, in iOS 10, Apple introduced a new system that allows apps to run silently in the background to process new push notifications before the device displays them.
The system allows applications that receive push notifications to decrypt the incoming payload and download additional content from their servers to enrich it before it is served to the user. When this process is completed, the application terminates again.
Through testing, Musk found that many apps abuse this feature, treating it as an opportunity to transmit device data back to their servers. Depending on the app, this includes system uptime, locale, keyboard language, available memory, battery status, storage usage, device model, and screen brightness.
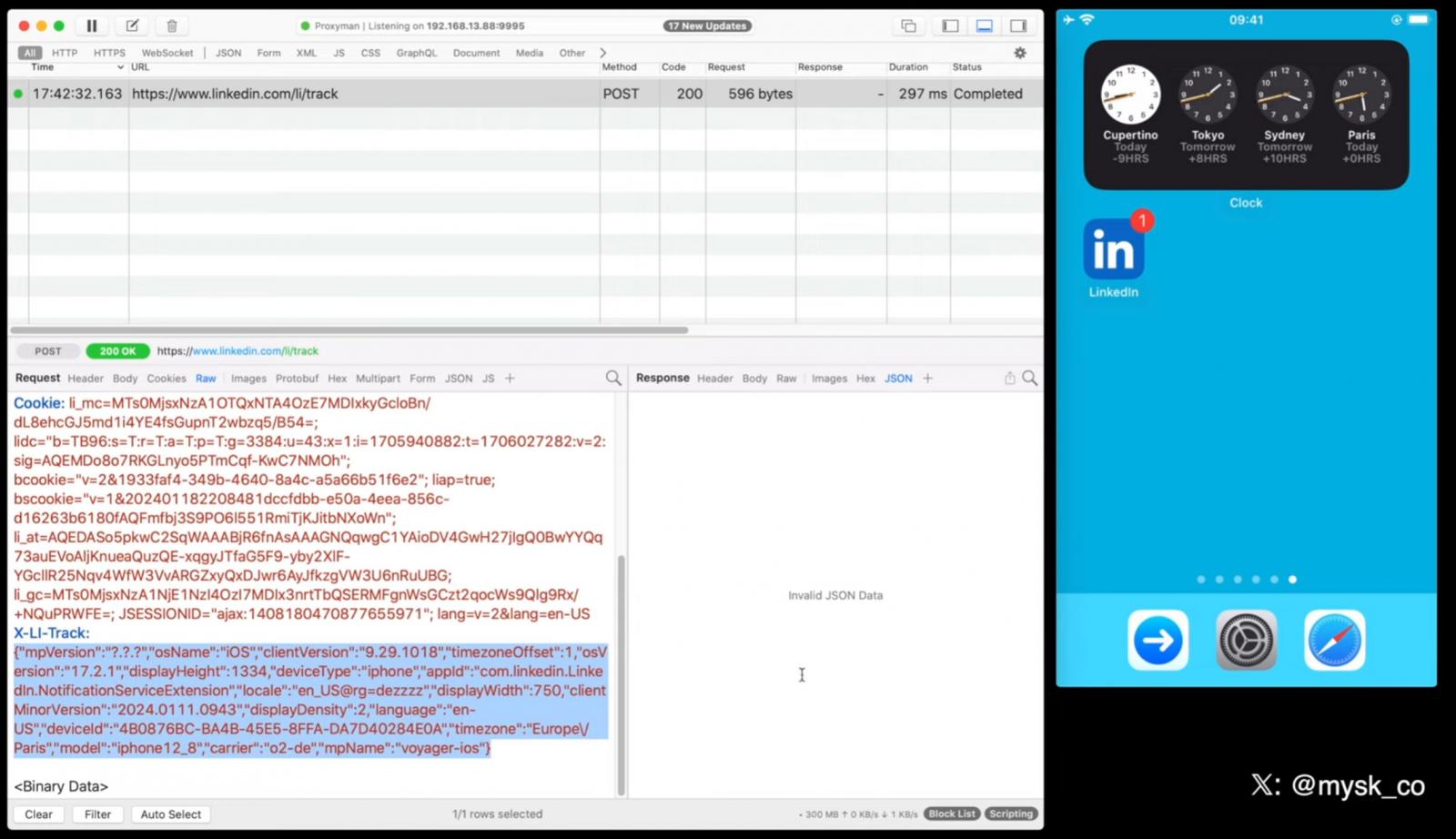
Source: Musk
The researcher believes that this data can be used to fingerprint/profile users, allowing for persistent tracking, which is strictly prohibited in iOS.
“Our tests show that this practice is more common than we expected. The frequency with which many apps send device data after being triggered by a notification is incredible,” Mysk explained in a post on Twitter.
Mysk created the following video showing the exchange of network traffic while receiving push notifications from TikTok, Facebook, X (Twitter), LinkedIn, and Bing.
Apps were found to be sending a wide range of device data to their servers using services like Google Analytics, Firebase or their own proprietary systems.
BleepingComputer reached out to Microsoft, X, Apple, TikTok and LinkedIn about their apps harvesting user data, but a response was not immediately available.
Mitigating the problem
Apple will fill the gap and prevent further abuse of wake-up push notifications by tightening restrictions on the use of the Device Signals API.
Mysk told BleepingComputer that starting in spring 2024, apps will be required to declare precisely why they need to use exploitable fingerprinting APIs.
These APIs are used to retrieve information about the device, such as disk space, system boot time, file timestamps, active keyboards, and user defaults.
If apps don’t properly declare their use of these APIs and what they’re used for, Apple says they’ll be rejected from the App Store.
Until that happens, iPhone users who want to avoid this fingerprint should disable push notifications entirely. Unfortunately, silencing notifications will not prevent abuse.
To disable notifications, open the ‘settings“go to”Notifications,’ select the app you want to manage notifications for and tap the disable switch ‘Allow notifications.’
In December, it was revealed that governments were demanding records of push notifications sent through Apple and Google servers as a way to spy on users.
Apple said it was barred from sharing any information about those requests by the US government and has since updated its transparency report.