Key operations
- Check app permissions regularly to control access to your camera, microphone, and files.
- Use Android’s privacy dashboard to monitor app permissions and limit malicious access.
- Remove unused apps and install them only from certified sources to protect your data.
Smartphones can do anything these days. Unfortunately, they can track it all. Smartphones have become a gold mine for data mining, but you’re not powerless — there are things you can do to make yours less accessible and valuable to those who want to profit from your activity.
Monitor your phone’s permissions
There are certain parts of your phone that apps must request permission to access. The app can’t open the camera unless you give it permission first. It cannot access the microphone. It cannot search your files.
Some of the apps that came with your phone may have permissions that you want to revoke, or you may have granted unwanted permissions to apps that you installed without paying special attention. You can change this by going to Settings > Security & privacy > Privacy > Permission manager.
Check out the privacy dashboard
As of Android 12, phones come with a feature known as the Privacy Dashboard. The privacy dashboard shows not only which apps have which permissions, but also how often and how recently they’ve been accessed. You can click on an app that appears to be abusing your privileges and deny access to it in the future.
Go to Settings > Security & Privacy > Privacy > Privacy Dashboard. Here’s how to access the privacy dashboard on a Samsung device.
Stop Google from collecting app data
When you first set up your Android device, if you answer yes to every question Google asks during setup, you’ll be giving the search giant a lot of information about you. Fortunately, you can tell Google not to collect this data. In some cases, like your Internet and YouTube browsing history or your location data, you can even tell Google to delete it. You can also set an automatic deletion schedule so that Google can save only recently generated data.
You can check these options by going to Settings > Security & privacy > Privacy > Activity controls.
Revoke permissions for unused apps
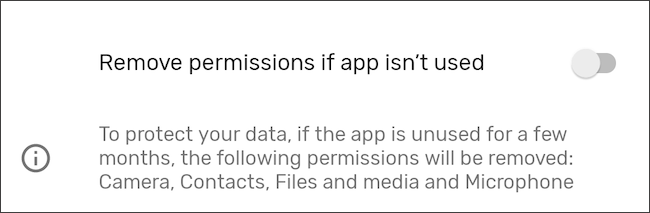
While it’s useful to occasionally check permissions every few months, it’s often not something we’ll remember to do. Fortunately, Android can automatically revoke permissions for apps that haven’t been used in a while.
On newer phones, this feature may already be enabled. To be sure, go to Settings > Apps and select an app. Scroll down to “Pause app activity if not in use” and activate the toggle. In addition to revoking permissions, this will also delete temporary files and stop notifications from said app.
On a Samsung device, the steps are the same, but the text has been changed to “Remove permissions if the app is not used.”
Uninstall unused applications
Many apps that we want or need collect a lot of data in the background. Some social networking, video streaming, shopping, photo editing, and other such apps can track what we do with our phone even when we’re not using it. We can quietly accept this when an app provides functionality that we use frequently, but if we no longer use the app, there’s no reason to let it continue to quietly siphon that data.
Scroll through your app drawer and note which apps you no longer use—then remove them. You can do this by long-pressing the app icon and selecting “App info”. Then press the uninstall button. On some phones, you can simply press the icon and select “Uninstall”.
Before installing, check the privacy of the application in Exodus
Permissions tell you a lot, but they don’t tell you the whole story. They tell you the mechanisms an app can use for tracking, but they don’t tell you if the app actually is. That’s where Exodus comes in. This is an Android app review service that comes from a non-profit organization based in Europe.
You can check if an app contains known trackers by going to the Exodus search tool and entering the name of the app. Exodus also offers a free, open source app that can automatically scan apps already on your device. The Exodus app is available on the Play Store and on F-Droid.
Only install apps from trusted sources
Out of the box, you can only install apps from pre-certified app stores like Play Store and Galaxy Store. If you try to install an Android APK file directly from your web browser or from a third-party source like TapTap, your phone will try to block this installation. This is because many malicious apps are distributed as APKs that would not be safely allowed in certified app stores.
For most people, sticking to default stores is a pretty good rule of thumb. Still, that doesn’t mean people, especially tech users, should never install apps from alternative places (some third-party sources like the free, open-source F-Droid repositories are arguably safer software sources than the Play Store). Rather check carefully and be sure to only install software from places you can trust.
Review app permissions before installation
You can actually see what permissions an app will require right in the Play Store before you even install it. This way, a greedy program will never even set foot on your device.
Scroll down to “About this app” in the Play Store list Then scroll down again to “App permissions” and tap “See more”. Here you can see the permissions that the app will request access to after installation.
Read the app’s Privacy Policy
Many apps come with privacy policies, especially if the app is an anchor for an online service. While it’s tempting to check the necessary boxes during the initial launch and move on with your life, at least take a quick look at the privacy policy. Sometimes you’ll see something you’re really not comfortable with.
A smart home app, for example, may indicate that it not only collects your IP address and your physical location, but that it may share this information with third parties for advertising purposes. That means you’re not just giving that information to one company, but to vendors, data brokers, or tech giants like Google and Facebook, who are known to buy data from other sources. The privacy policy won’t come right out and say its service is suspect, but it can certainly imply that.
Taking all these steps won’t guarantee your privacy, but it will help. To go further, you can use a VPN to mask your IP address. You can also use email aliases when signing up for new applications. And if you really want to make sure nothing is happening in the background, you can install a firewall like NetGuard.