Therefore, for these environments, data leakage protection will target locally stored assets such as source code, credentials, and potentially sensitive data.
Risk assessment of locally stored data
Let’s first quickly go back into the history of ICT and look at an often cited one A 2010 reference study titled “The Billion Dollar Lost Laptop Problem”. The study looked at 329 organizations over 12 months and reported that more than 86,000 laptops were stolen or lost, resulting in a loss of $2.1 billion, an average of $6.4 million per organization.
In 2010, the use of the Cloud as a medium for corporate data storage was in its early stages; therefore, the metrics for determining the cost and impact of losing a business laptop would likely look very different today.
For example, for many business functions that were likely to be affected at the time, Cloud applications have provided a solution today by removing sensitive data from employee laptops. This has largely shifted the laptop security debate to protecting the credentials needed to access business resources in the cloud (or self-hosted), rather than protecting locally stored data itself.
Picture 1: In 2024, most business productivity data has already been moved to the cloud. During the 2010s, a significant step was CRM data, which ultimately greatly reduced the risk of corporate data leakage.
There is, however, a notable exception to the above shift in technology: the environments used for code development. For practical reasons, the devices used for development today have a replica of the project’s source code, along with corporate secrets such as credentials, web tokens, cryptographic keys, and perhaps strategic data for training machine learning models or testing algorithms.
In other words, there is still a lot of interesting data stored locally in development environments that guarantees protection against loss or theft. Therefore, the interest in providing development environments has not waned.
There are a variety of reasons for malicious actors to seek assets in these environments, from access to corporate intellectual property (check out Grand Theft Auto 6 hack)to understanding the existing vulnerabilities of the application in order to compromise its operation.
Despite all this potential fallout from hacking a single developer’s environment, few companies today can pinpoint exactly where replicas of their source code, secrets and data reside (hint: probably on all devices of their distributed workforce) and are poorly protected against laptop loss or looming threats from within. Recall that using any online or self-hosted source code repository such as GitHub does not resolve any replicas in developer environments. This is because developers need local replicas to update their code before submitting it back to the online Git repository. Therefore, protecting these environments is a problem that grows with the number of developers working in an organization.
Use cases for virtual desktops and secure laptops for developers
The desire to remove data from the developer environment is prevalent in many regulated industries such as finance and insurance. One of the most common approaches is to use development machines that are accessed remotely.
Citrix and VMware have been key players in this market enabling developers to remotely access virtual machines hosted by an organization. In addition, these platforms implement data loss prevention mechanisms that monitor user activities to prevent data leakage.

Figure 2: Left – developers for remote access to virtual machines hosted by the organization. True – Virtualization has evolved from emulating machines to processes, which are used as the basis for DevOps.
Running and accessing a virtual machine remotely for development has many drawbacks, especially in developer productivity. One reason is that the streaming mechanism used for remote desktop access requires significant bandwidth to be truly usable and often results in irritating delays when writing code.
The entire apparatus is also complex to set up, as well as expensive to maintain and operate for the organization. In particular, using a virtual machine is a rather difficult mechanism that requires significant computing resources (and therefore costs) to operate.
Finally, such a general purpose setting; i.e. it is not designed specifically for code development and requires the installation of the full suite of development tools.
For the reasons explained above, many organizations have reverted to securing developer laptops using endpoint security mechanisms that implement measures to prevent data loss. In the same way as for the VDI counterpart, this is also often an expensive solution as such laptops have complex setups. When engaging remote development teams, organizations often mail these laptops at great expense, complicating the maintenance and monitoring process.
The case for secure cloud development environments
Recently, virtualization has evolved from the emulation of entire machines to the granularity of individual processes technology of software containers. Containers are convenient for code development because they provide a minimal and sufficient environment for compiling typical applications, especially web-based ones. In fact, compared to virtual machines, containers run in seconds instead of minutes and require far fewer computing resources to execute.
Containers are typically tools used locally by developers on their devices to isolate software dependencies associated with a particular project in such a way that source code can be compiled and executed without disturbing potentially unwanted settings.
The great thing about containers is that they don’t have to remain a locally used development tool. They can be run online and used as an alternative to a virtual machine. This is the basic mechanism used to implement a Cloud development environment (CDE).
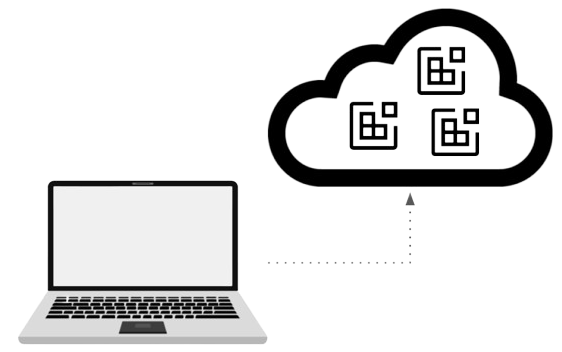
Figure 3: Containers can be run online and become a lightweight alternative to a virtual machine. This is the basic mechanism for implementing the Cloud Development Environment.
Running containers online is one of the most exciting recent trends in virtualization in line with DevOps practices where containers are key to enabling efficient testing and deployment. CDEs are accessed online from the IDE via a network connection (Microsoft Visual Studio Code has feature as explained here) or using Cloud IDE (an IDE that runs in a web browser such as Microsoft Visual Studio Code, Eclipse of Theia, and others.)
Cloud IDE gives the developer access to CDE with the advantage of not having to install any environment on the local machine. Access to the remote container is done transparently. Compared to the remote execution desktop, as discussed previously, the discomfort of environment streaming does not apply here since the IDE is executed as a web application in the browser. Therefore, the developer will not suffer display delays especially in low-bandwidth environments such as VDI and DaaS. Bandwidth requirements between IDE and CDE are low because only textual information is exchanged between them.
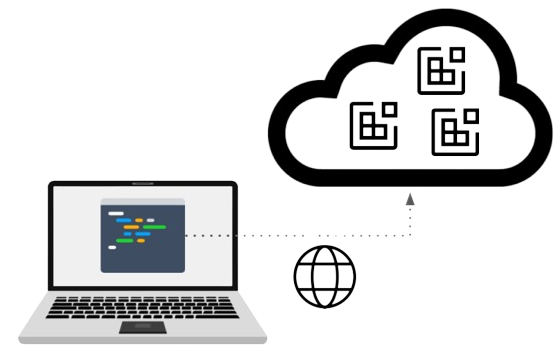
Figure 4: Accessing the remote container is done using an IDE running in a web browser; therefore, developers will not suffer display delays, especially in low-bandwidth environments
As a result, in the specific context of application development, the use of CDEs is a lightweight mechanism for removing development data from local devices. However, this still falls short of the security provided by Citrix and other VDI platforms, as CDEs are designed for efficiency, not security. They do not provide any data loss prevention mechanism.
Herein lies the case for deploying secure cloud development environments: CDEs with data loss prevention provide a lightweight alternative to using VDI or secure development laptops, with the added benefit of an improved developer experience. The resulting platform is a secure cloud development platform.
By using such a platform, organizations can significantly begin to reduce the cost of providing secure development environments for their developers.
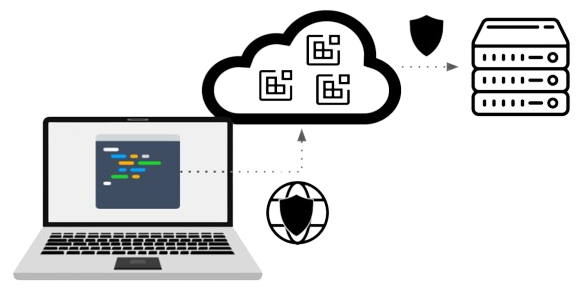
Figure 5: To become a substitute for VDI or secure laptops, Cloud Development Environments must include security measures against data leakage.
Moving from virtual desktops to secure cloud development environments
As a conclusion to this discussion, below I briefly recap the various steps for building a secure cloud-based development platform that combines an efficient CDE infrastructure with end-to-end data theft protection, leading to a secure CDE.
Initially, secure developer laptops were used to directly access corporate resources sometimes using a VPN when outside the IT perimeter. According to the benchmark study I mentioned at the beginning of this article, 41% of laptops routinely contained sensitive data according to the study I mentioned at the beginning of this article.
Next, the use of virtual machines and early access to web applications allowed organizations to remove data from local laptop storage. But developing code on remote virtual machines was, and still is, laborious.
Recently, the use of lightweight container-based virtualization has enabled faster access to networked development environments, but all current vendors in this space lack data security because the primary use case is productivity.
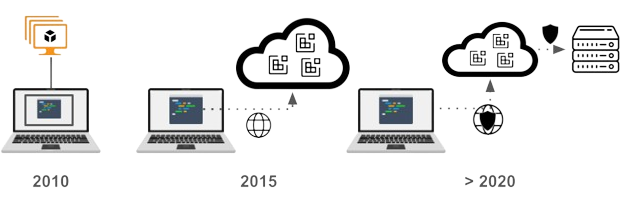
Figure 6: An overview of the technological evolution of the mechanisms used by organizations to provide secure development environments over the past decade.
Finally, the secure Cloud Development Environment platform (as shown in the far right image below) illustrates the closest incarnation of a secure development laptop. Secure CDEs benefit from the experiences of pioneering companies like Citrix, seizing the opportunity to decouple development environments from traditional hardware. This separation allows for a blend of infrastructure efficiency and security without compromising the developer experience.