
Google has launched a new pilot program to fight financial fraud by blocking sideloading of Android APK files that require access to risky permissions.
APK (Android Package) is a file format used to distribute Android applications for installation into the operating system. These files are usually distributed through third-party websites, which allow you to install apps outside of Google Play.
However, because these external sites do not check for malicious application behavior, they may include malware, spyware, and other threats.
Due to the complexity and difficulty of uploading bad apps to Google Play, threat actors are turning to social engineering, using various baits to convince targets to download malicious apps from external, unverified sources.
These APKs can trick victims into revealing sensitive personal and financial information, allowing threats to commit financial fraud.
Google says that during 2023, fraud cost users more than $1 trillion in losses, and 78% of users surveyed (by the Global Anti-Scam Alliance) said they had experienced at least one fraud attempt.
Blocking risky applications
In October 2023, Google Play Protect received a new security feature that scans APKs downloaded from app stores and third-party websites in real time.
The feature has been rolled out in major markets including India, Thailand, Brazil and Singapore, and is expected to reach more countries this year.
Google says the feature has identified 515,000 unwanted apps and warned against or blocked 3.1 million installations.
To further strengthen protection against unwanted apps, Google is now running a pilot in Singapore where it will directly block the installation of APKs that require access to the following risky permissions:
- RECEIVE_SMS – Attackers use this to intercept one-time passwords (OTPs) or authentication codes sent via SMS, allowing unauthorized access to victims’ accounts.
- READ_SMS – It is misused by attackers to read sensitive information, such as OTPs, banking messages or personal communications, without the user’s knowledge.
- BIND_Notifications – Attackers exploit this to read or dismiss notifications from legitimate apps, including security alerts or OTP notifications, potentially without the user noticing.
- Accessibility – This permission, intended to help users with disabilities, gives a malicious APK application broad access to control the device and its functions. Attackers abuse it to track user actions, retrieve sensitive data, enter keystrokes and execute commands remotely, often leading to a complete compromise of the device.
“Based on our analysis of large rogue malware families that exploit these sensitive runtime permissions, we found that more than 95 percent of installations come from download sources from the Internet,” Google’s report said.
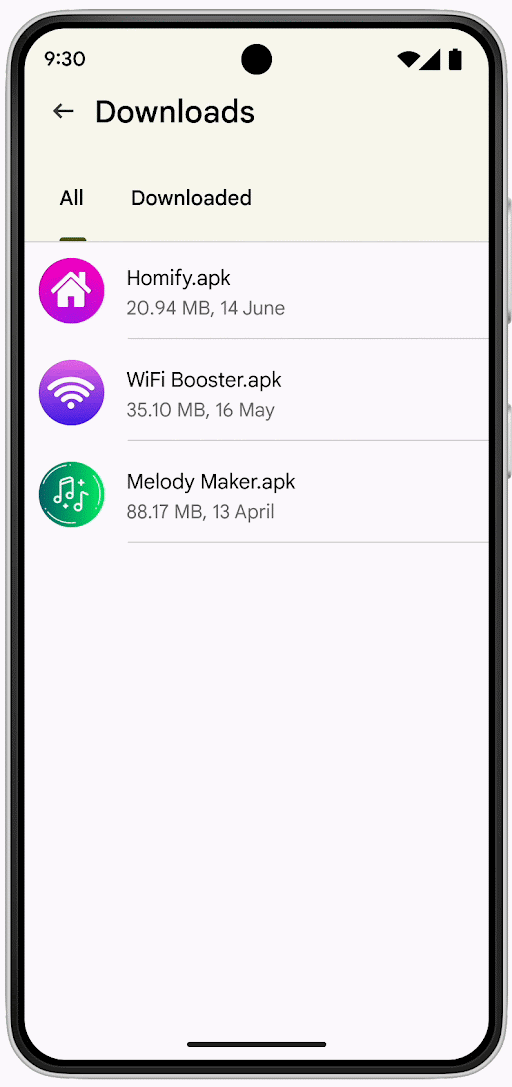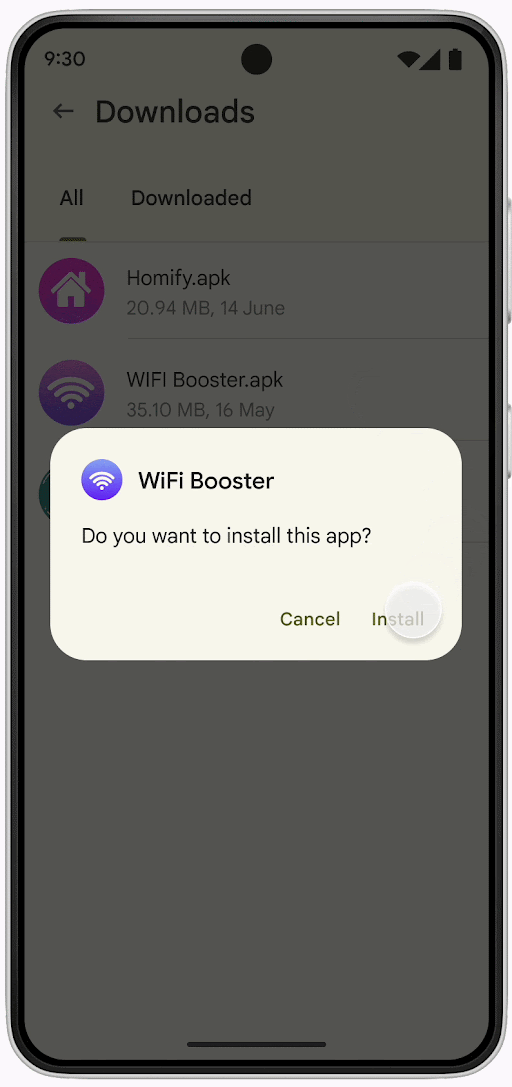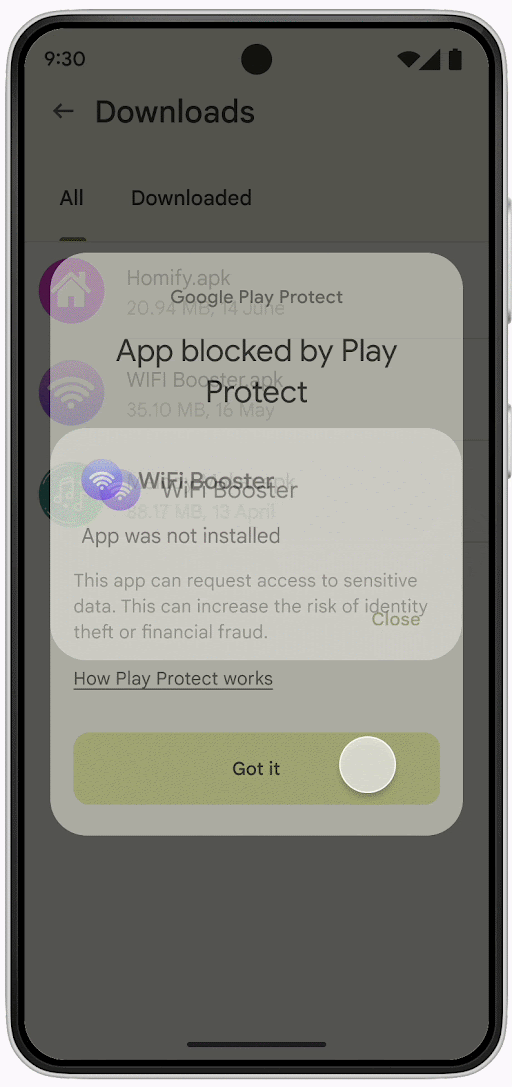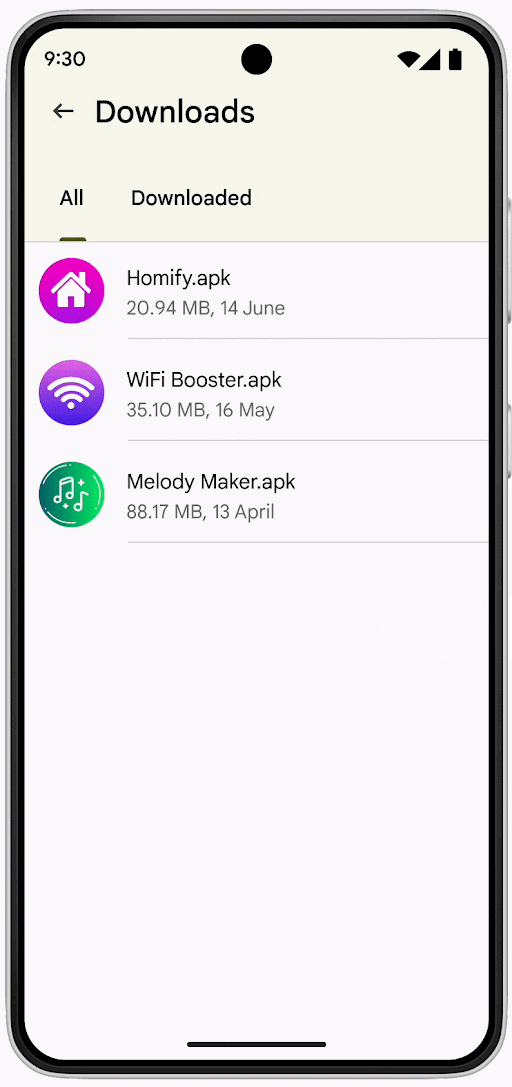
“During the upcoming pilot, when a user in Singapore tries to install an app from an online sideloading source and any of these four permissions are declared, Play Protect will automatically block the installation with an explanation to the user.”
BleepingComputer asked Google about its plans to roll out this new protection feature to the rest of the world, and a spokesperson sent the following statement:
We’re constantly improving our protection to protect Android users around the world. Together with the Cyber Security Agency of Singapore (CSA), we will closely monitor the results of the pilot program to assess its impact and make adjustments as necessary.
We are open to expanding the pilot to other countries in the future if we see similar interest and user protection needs. – Google spokesperson
In the meantime, Android users are advised to avoid downloading APKs as much as possible, carefully check the permissions requested during app installation, and run Play Protect scans regularly
Update 2/8 – Added Google statement