
The Anatsa banking trojan targeted users in Europe by infecting Android devices via malware droppers located on Google Play.
Over the past four months, security researchers have observed five campaigns tailored to deliver malware to users in the UK, Germany, Spain, Slovakia, Slovenia and the Czech Republic.
Researchers at fraud detection firm ThreatFabric have noted an increase in Anatsa activity since November, with at least 150,000 infections.
Each attack wave is focused on specific geographic regions and uses dropper apps designed to reach the “Best New Free” categories on Google Play, giving them credibility and increasing their success rate.
The ThreatFabric report states that dropper apps now implement a multi-stage infection process and have evolved to abuse Android’s accessibility service to bypass security measures present in mobile operating system versions up to Android 13.
Last summer, ThreatFabric warned of another Anatsa campaign targeting Europe that also used dropper apps hosted on Google Play, primarily fake PDF viewer apps.
Anatsa dropper applications
In the latest Anatsa campaign, malware operators are using both PDF and fake cleaning apps that promise to free up space on the device by deleting unnecessary files.
One example ThreatFabric researchers point to is an app called ‘Phone Cleaner – File Explorer’, which has counted over 10,000 downloads.
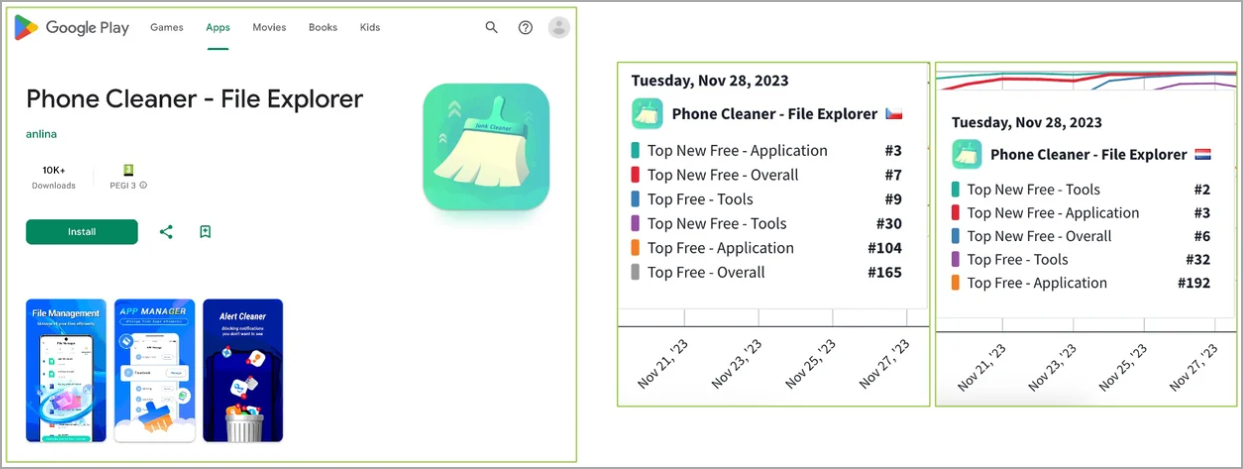
ThreatFabric told BleepingComputer that one Anatsa campaign also used another app called ‘PDF Reader: File Manager’, which saw more than 100,000 downloads.
At the time of writing, Google has removed all Anatsa dropper apps from the official Android store except PDF Reader, which is still available.

ThreatFabric researchers told us that the number of 150,000 downloads of the Anatsa dropper on Google Play is conservative and that the actual number would be closer to 200,000 because they used lower estimates for the total.
The five malicious applications are:
- Phone Cleaner – File Explorer (com.volabs.androidcleaner)
- PDF viewer – File Explorer (com.xolab.fileexplorer)
- PDF reader – viewer and editor (com.jumbodub.fileexplorerpdfviewer)
- Phone Cleaner: File Explorer (com.appiclouds.phonecleaner)
- PDF Reader: File Manager (com.tragisoap.fileandpdfmanager)
With Anatsa constantly launching new waves of attacks using fresh dropper apps, the total number of downloads is expected to rise further. It has already exceeded the 130,000 that Anatsa achieved in the first half of 2023.
Technical details
Technical insights from the ThreatFabric report reveal that dropper applications use a multi-stage approach to avoid detection, dynamically downloading malicious components from a command and control (C2) server.
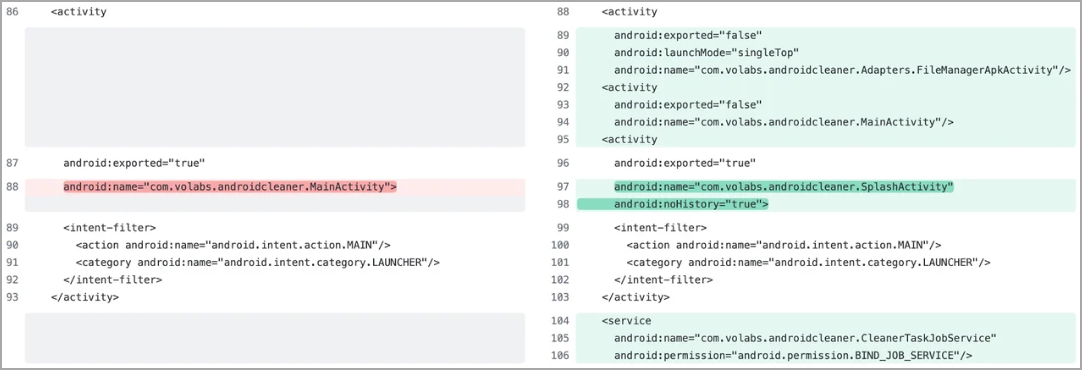
A notable strategy involves exploiting the AccessibilityService, historically a vector for malware to automate the installation of useful content without user interaction.
Malware that abuses this powerful Android service created to help users with disabilities happens frequently, despite Google’s recent policy updates that introduced restrictions to combat abuse.
Allowing Anatsa droppers to access the accessibility service was masked by the need to “hibernate battery draining apps”, which seems like a legitimate feature in the context of a cleaner app.
In one case, Threat Fabric discovered that a malicious code update was introduced a week after the dropper app was uploaded to Google Play and added user interface navigation parameters that match those of Samsung devices (One UI).
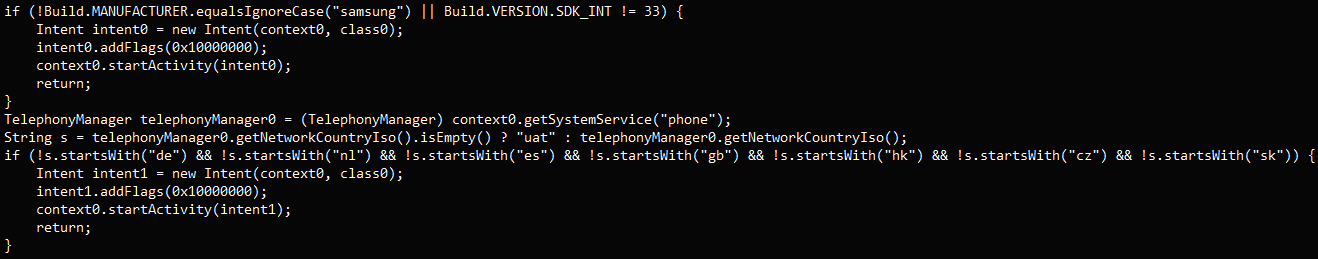
Other droppers used in the same campaign do not contain vendor-specific code, therefore targeting a wider variety of Android devices.
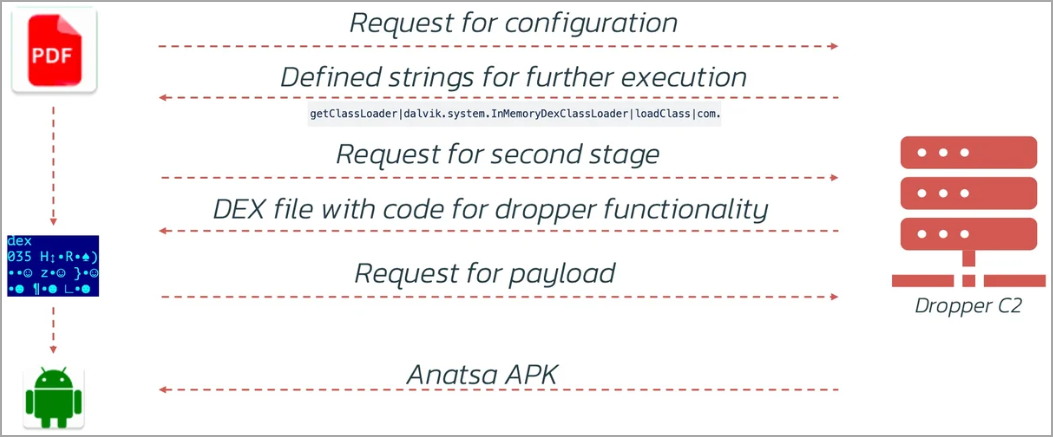
The malicious code update is downloaded from C2 in four different steps, which is likely a tactic to avoid detection and flagging by Google’s code review engines.
- Retrieving the configuration: Downloads the configuration from the C2 server that contains the bit strings for malicious code, avoiding immediate detection by hiding suspicious indicators.
- DEX file download: Retrieves a DEX file with malicious code responsible for installing payloads, activated by previously downloaded strings.
- Payload URL configuration: Downloads a configuration file with a payload URL, allowing attackers to update the payload link as needed.
- Load capacity installation: Uses the DEX file to download, install and run the Anatsa malware, completing the infection process.
The expansion of the Anatsa campaign is significant and comes with the risk of financial fraud. Android users are advised to carefully review the user ratings and history of the publisher before installing the app.
A good way to stay protected is to avoid performance, productivity, and secure messaging apps that don’t come from reputable vendors.
When installing new applications, it is highly recommended to check the list of requested permissions and deny those that are not related to the purpose of the application (eg, a photo editing application does not need access to the microphone).
When installing new apps, carefully study the requested permissions, especially those related to the accessibility service, which should be considered a red flag for potential malware threats.