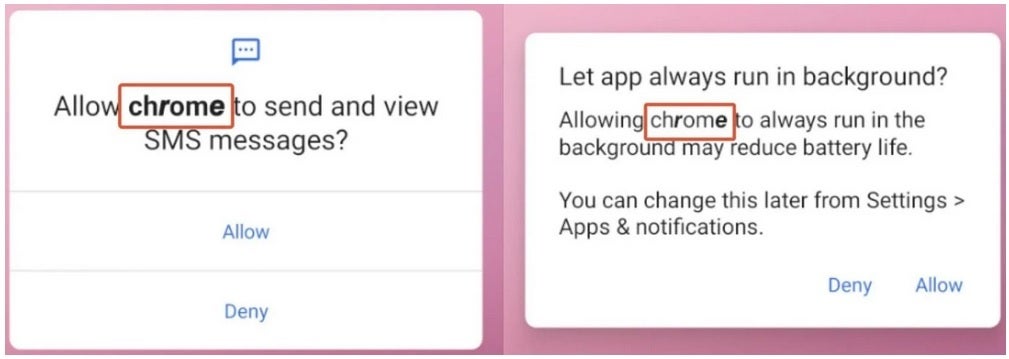
The fake permission requests appear to come from Google Chrome
McAfee says: “While the app is installed, their malicious activity starts automatically. We have already reported this technique to Google and they are already working on implementing mitigations to prevent this type of auto-execution in a future version of Android.”
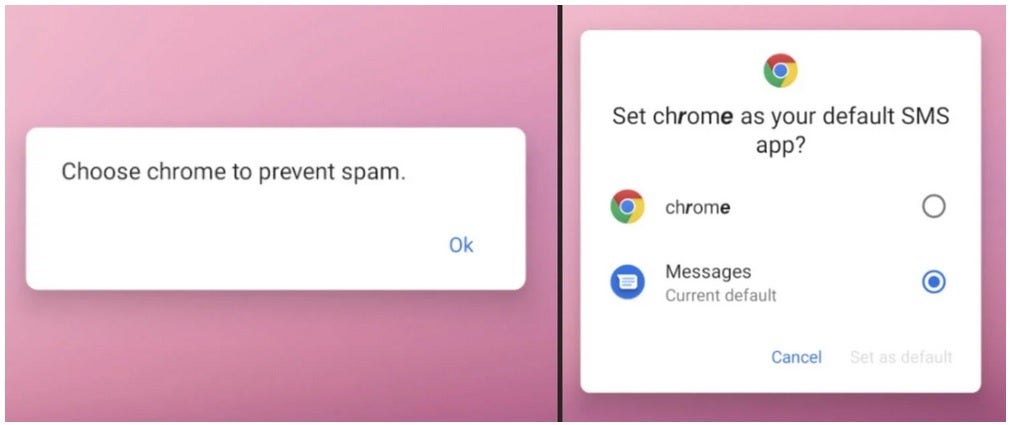
Another bogus permission request
Malicious apps send permission requests by pretending to come from Google Chrome asking for permission to send and view SMS (text) messages and asking permission for “Chrome” to run in the background. And the coup de grace is allowing “Chrome” to become your default SMS app. The malware, once granted all these permissions, is used to send photos, text messages, contact lists and information about the hardware you’re using (including your phone’s unique IMEI number) to the control server. Yes, it’s very scary.
McAfee says that because the victim requires minimal interaction, the new XLoader malware is even more dangerous than its predecessor. There is good news. An update from McAfee from a few weeks ago says that Android devices with Google Play Services are protected against this type of malware attack using Google Play Protect, which is enabled by default.