Android phone owners are urged to delete five suspicious apps that can steal your data, search your bank account and take control of all on your phone behind your back.
Google has moved dangerous apps from the Play Store, but this only prevents people who haven’t installed the software before from downloading it to their phone – it doesn’t help if these problematic apps are already on your phone.
Security researchers have warned that many malware-ridden apps have made it to the top three of the Google Play Store’s Top New Free chart, making them all appear credible and driving hundreds of thousands of downloads in the UK and mainland Europe.
Hidden inside these dangerous Android apps – disguised as innocent names like Phone Cleaner and PDF Viewer – is a banking Trojan called “Anatsa”. It was built to target users in the United Kingdom, Germany, Spain, Slovakia, Slovenia, and the Czech Republic.
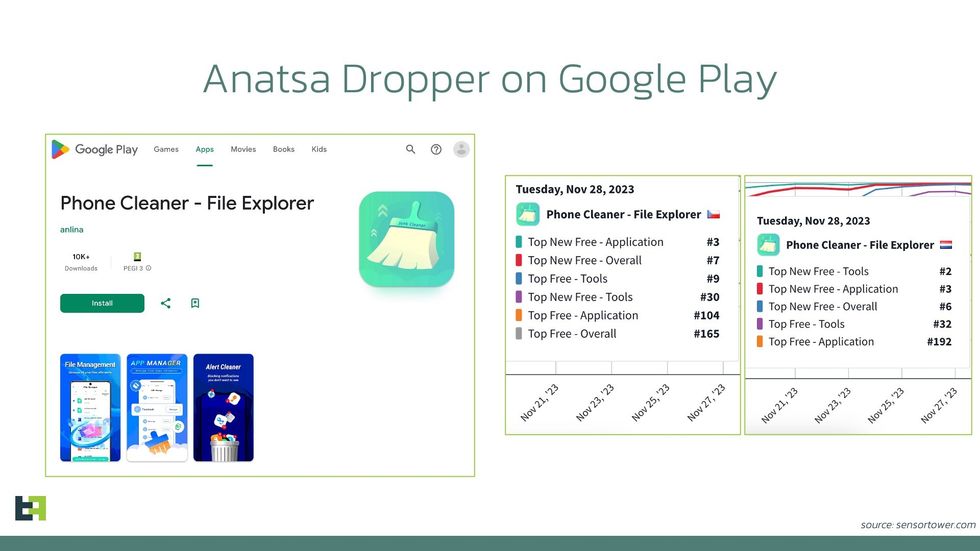
Phone Cleaner – File Explorer is one of the Android apps that security researchers found sneaked a banking trojan into the Play Store. It took third place on the Top New Free chart
THREAT FABRIC | GOOGLE PLAY STORE
Security researchers at Threat Fabric have been tracking this type of banking malware since June 2023. Unsuspecting Android users downloaded the rogue malware between 150,000 and 200,000 times before Google removed the problematic apps from its digital storefront.
If you have downloaded any of these apps, hackers can remotely take control of your phone and perform tasks behind your back. Anatsa allows them to download personal information from your device and make payments from popular banking applications.
Threat Fabric researchers have warned Samsung smartphone owners to be extra cautious about the threat. That’s because the malicious code discovered in these Android apps seemed to suggestfraudsterstailored to suit user interfacial elements specific to Samsung hardware.
“This suggests that threat actors initially developed and tested their code exclusively for Samsung devices,” noted experts at detailed report about the revival of Anatsa.
The apps that you will need to manually remove from your phone are the following…
- Phone Cleaner – File Explorer
- PDF viewer – File Explorer
- PDF reader – viewer and editor
- Phone Cleaner: File Explorer
- PDF Reader: File Manager
A Google spokesperson said: “All apps identified in the report they were removed from Google Play. Android users are automatically protected against known versions of this malware using Google Play Protect, which is turned on by default on Android devices with Google Play Services.
“Google Play Protect can warn users or block apps that are known to exhibit malicious behavior, even when those apps come from sources outside of Play.”
Deleting the apps should remove the threat from your phone. If you receive an alert from Google’s Play Protect service, always check what triggered the alert and take action.
Worryingly, the team at Threat Fabric sees no end to malicious apps trying to sneak Anatsu onto your Android phone. IN blog postthe researchers warned: “Based on this pattern, we to predict continuation of this campaign, with the appearance of new droppers in the official store and expansion to additional target regions.”
Experts believe banks should do more to warn customers about the dangers of downloading untrusted apps. They posted: “Financial organizations should urgently educate their customers about the risks of installing apps, even from official stores, and warn against enabling AccessibilityService for apps thatt Don‘t require it for themr alleged operationn.s.
“In cases where users report unusual device behavior or unrecognized transactions, we advise institutions to inquire about recent activity such as newly installed apps and any permissions that have been granted, particularly in relation to the AccessibilityService.”