
Over 15 free VPN apps on Google Play were found using a malware development kit that turned Android devices into unwitting home proxy servers, likely used for cybercrime and shopping bots.
Residential proxies are devices that route Internet traffic through devices located in the homes of other remote users, making the traffic legitimate and less likely to be blocked.
Although they have legitimate uses for market research, ad verification, and SEO, many cybercriminals use them to disguise malicious activities, including ad fraud, spamming, identity theft, credential spoofing, and password hashing.
Users can voluntarily register with proxy services to get monetary or other rewards in return, but some of these proxy services use unethical and shady ways to secretly install their proxy tools on people’s devices.
When installed surreptitiously, victims will be robbed of their Internet bandwidth without their knowledge and risk legal trouble as they appear as a source of malicious activity.
Proxy Android VPN app
A report released today by HUMAN’s Satori threat intelligence team lists 28 apps on Google Play that secretly turned Android devices into proxy servers. Out of these 28 apps, 17 are featured as free VPN software.
Satori analysts report that all the malicious apps used LumiApps’ software development kit (SDK) that contained “Proxylib”, a Golang library for running proxies.
In May 2023, HUMAN revealed the first PROXYLIB carrier app, a free Android VPN app called “Oko VPN”. The researchers later found the same library used by the Android app monetization service LumiApps.
“At the end of May 2023, Satori researchers noticed activity on hacker forums and new VPN applications referencing the Monetization SDK, lumiapps[.]io”, explains Satori’s report.
“Upon further investigation, the team determined that this SDK has exactly the same functionality and uses the same server infrastructure as the malicious applications analyzed as part of the investigation into the earlier version of PROXYLIB. “
Subsequent investigation revealed a set of 28 apps that used the ProxyLib library to turn Android devices into proxies, which are listed below:
- Simple VPN
- Keyboard with animations
- Blaze Stride
- Byte Blade VPN
- Launcher for Android 12 (by CaptainDroid)
- Launcher for Android 13 (by CaptainDroid)
- Launcher for Android 14 (by CaptainDroid)
- CaptainDroid Feeds
- Free Old Classic Movies (by CaptainDroid)
- Phone Comparison (by CaptainDroid)
- Fast Fly VPN
- Fast Fox VPN
- Fast Line VPN
- Funny Char Ging animation
- Limousine edges
- VPN around
- Phone application launcher
- Quick Flow VPN
- An example of a VPN
- Secure the Thunder
- Safety shine
- Fast surfing
- Swift Shield VPN
- Turbo Track VPN
- Turbo Tunnel VPN
- Yellow Flash VPN
- VPN Ultra
- Start VPN
LumiApps is an Android app monetization platform that states its SDK will use a device’s IP address to load web pages in the background and send the fetched data to businesses.
“Lumiapps helps companies collect information that is publicly available on the Internet. It uses the user’s IP address to load several web pages in the background from known websites,” the LumiApps website states.
“This is done in a way that never interrupts the user and is fully GDPR/CCPA compliant. The websites are then sent to companies who use them to improve their databases, offering better products, services and prices.”

Source: BleepingComputer
However, it is not clear whether the developers of the free apps knew that the SDK was turning their users’ devices into proxy servers that could be used for unwanted activities.
HUMAN believes the malicious applications are linked to the Russian residential proxy provider ‘Asocks’ after observing links made to the proxy provider’s website. The Asocks service is usually promoted to cybercriminals on hacking forums.
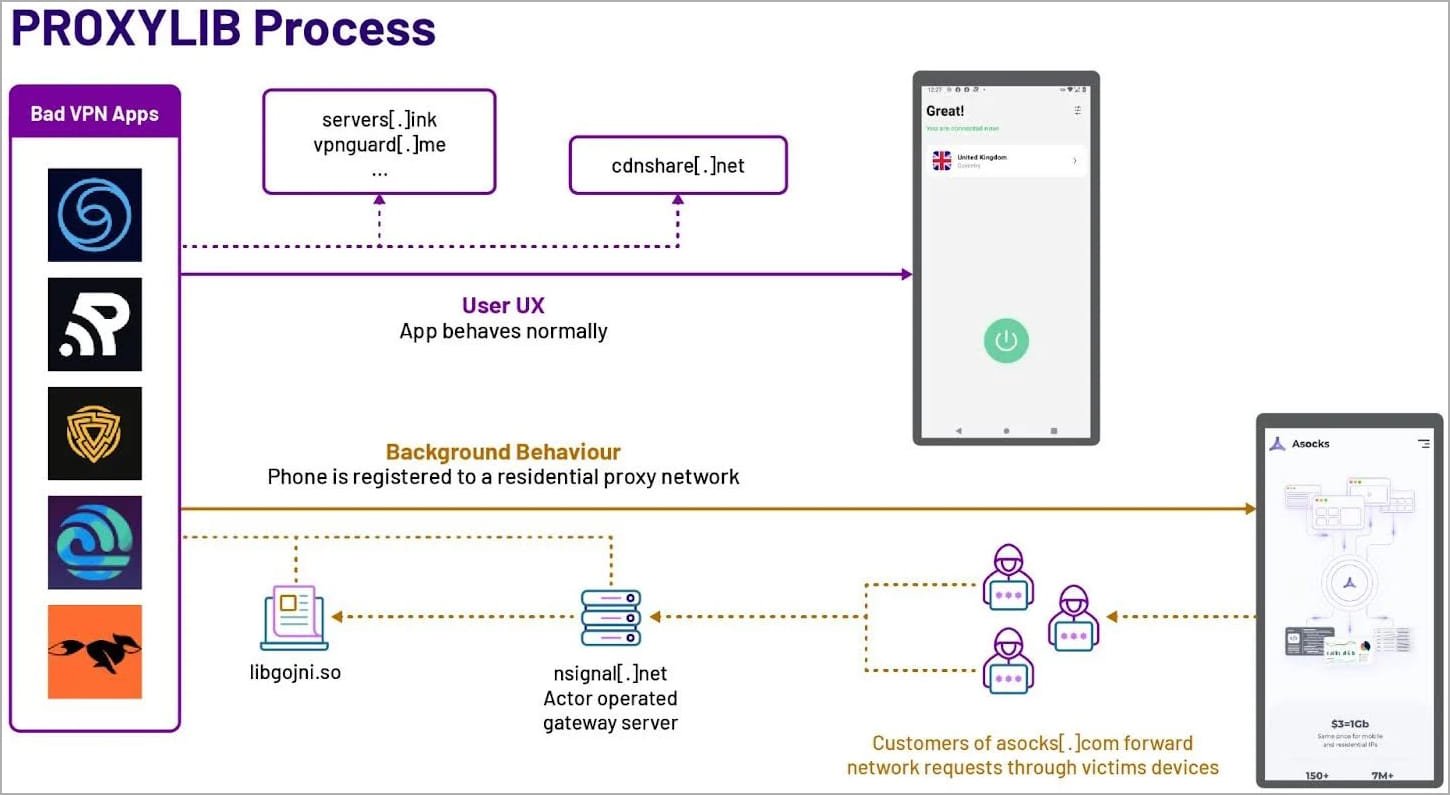
Source: HUMAN
In January 2024, LumiApps released the second major version of its SDK along with Proxylib v2. According to the company, this solved “integration issues”, and now supports Java, Kotlin and Unity projects.
Following HUMAN’s report, Google removed all new and remaining apps using the LumiApps SDK from the Play Store in February 2024 and updated Google Play Protect to detect LumiApp libraries used in apps.
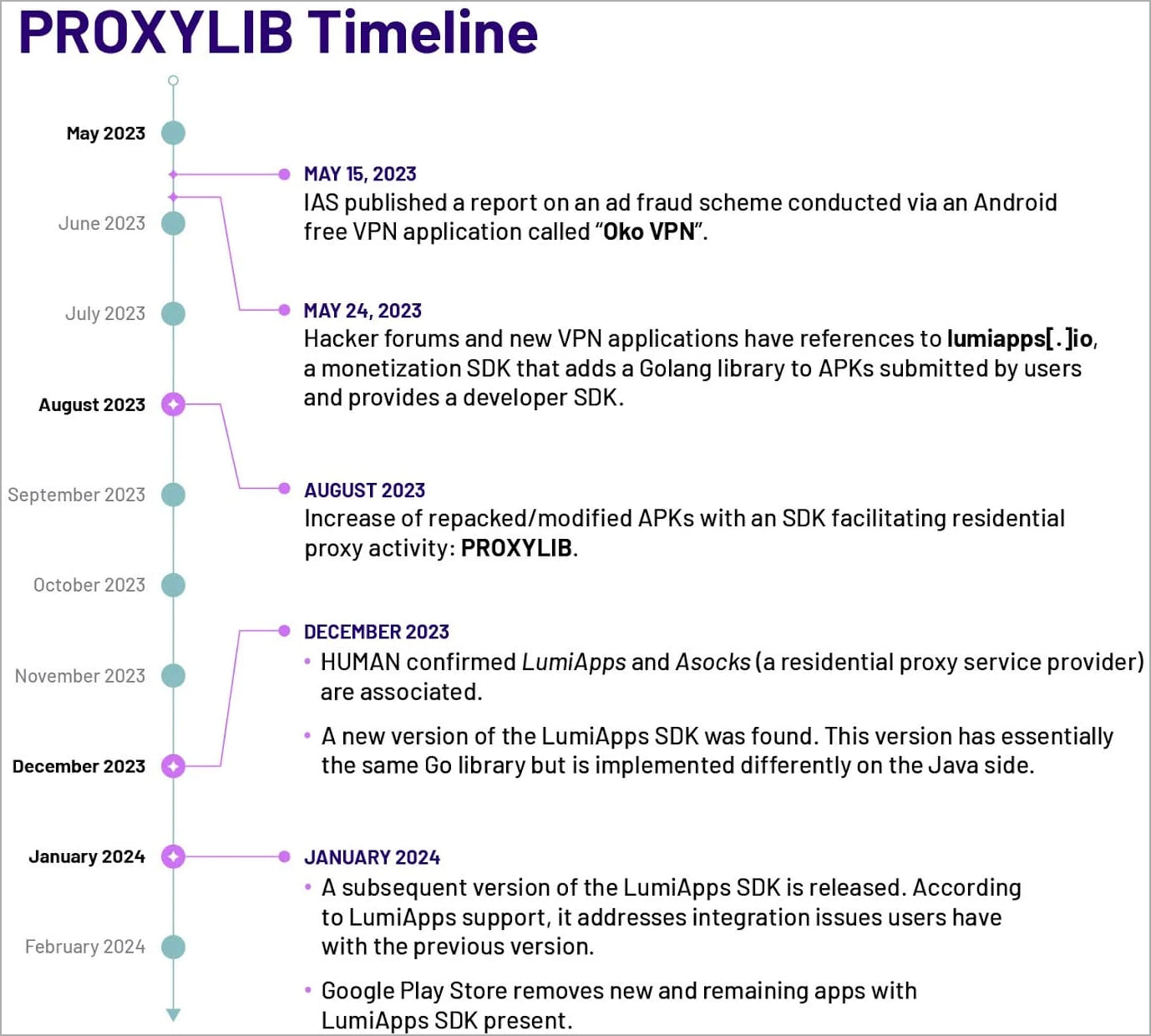
Source: HUMAN
Meanwhile, many of the apps listed above are now available again on the Google Play Store, presumably after their developers removed the contentious SDK. Sometimes they were posted from different developer accounts, potentially indicating previous account bans.
Source: BleepingComputer
BleepingComputer has reached out to Google for comment on the status of currently available apps using the same names and whether they are now safe, but we have yet to hear back.
If you’ve been using one of the apps listed, updating to the latest version that doesn’t use that particular SDK will stop the proxy activity. However, out of an abundance of caution, it may be safer to remove them entirely.
If the app has been removed from Google Play and there is no secure version, we recommend uninstalling it. Play Protect should also warn users in this case.
Finally, it’s probably safer to use paid VPN apps instead of free services since many products in the latter category are more likely to implement indirect monetization systems, including data collection/sale, advertising, and proxy enrollment.