.jpg)
The latest version of the PixPirate Android banking trojan uses a new method to hide on phones while remaining active, even if its dropper app has been removed.
PixPirate is a new Android malware first documented by the Cleafy TIR team last month that targeted Latin American banks.
Although Cleafy noted that a particular download application runs the malware, the report did not delve into its innovative hiding or persistence mechanisms, or whether they were introduced only recently.

A new report from IBM explains that contrary to the standard malware tactic of trying to hide its icon, which is possible on Android versions up to 9, PixPirate does not use a launcher icon. This allows the malware to remain hidden on all recent Android releases up to version 14.
However, not using the icon at all creates the practical problem of the victim not being able to run the malware.
IBM Trusteer researchers explain that new versions of PixPirate use two different applications that work together to steal information from devices.
The first application is known as a ‘downloader’ and is distributed via APKs (Android Package Files) which are spread via phishing messages sent on WhatsApp or SMS.
This download application requires access to risky permissions after installation, including accessibility services, and then proceeds to download and install another application (called ‘droppee’), which is the encrypted PixPirate banking malware.
The ‘droppee’ app does not declare a main activity with “android.intent.action.MAIN” and “android.intent.category.LAUNCHER” in its manifest, so no icon appears on the home screen, making it completely invisible.
Instead, the droppee application exports a service that other applications can connect to, which the downloader connects to when it wants to launch the PixPirate malware.
In addition to a dropper application that can launch and control malware, these triggers can be device startup, connectivity changes, or other system events that PixPirate listens for, allowing it to execute in the background.
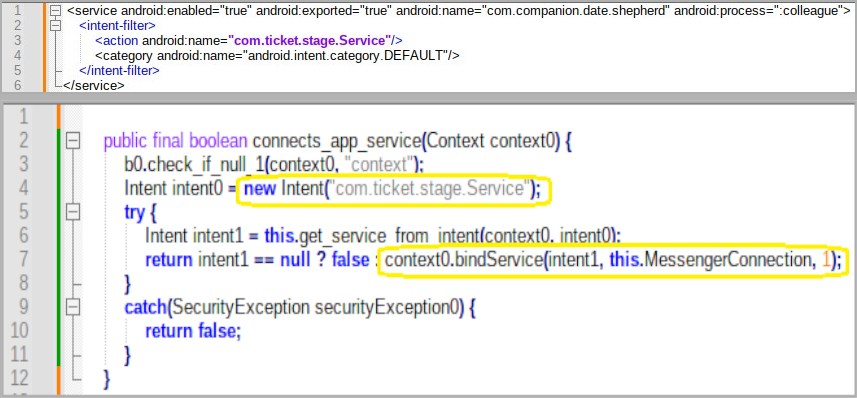
“Droppee has an exported service called “com.companion.date.sepherd” and contains an intent filter with a custom action of ‘com.ticket.stage.Service.'” IBM analysts explain.
“When a downloader wants to start a droppee, it creates and connects to this droppee service using the “BindService” API marked “BIND_AUTO_CREATE” which creates and starts the droppee service.”
“After creating and connecting the droppee service, the droppee APK is launched and starts working.”
Even if the victim removes the download application from the device, PixPirate can continue to run based on various events on the device and hide its existence from the user.
Hidden money transfers
The malware targets Brazilian instant payment platform Pix, attempting to divert funds to attackers by intercepting or initiating fraudulent transactions.
IBM says Pix is very popular in Brazil, where more than 140 million people use it to conduct transactions that exceeded $250 billion as of March 2023.
PixPirate’s RAT capabilities allow the entire fraud process to be automated, from capturing user credentials and two-factor authentication codes to executing unauthorized Pix money transfers, all in the background without the user’s knowledge. However, this requires accessibility service permissions.
There is also a fallback manual control mechanism when automated methods fail, giving attackers another channel to perform device fraud.
Cleafy’s report from last month also highlighted the use of push notification malvertising and the ability of malware to disable Google Play Protect, one of Android’s core security features.
Although PixPirate’s method of infection is not new and can be easily fixed by avoiding APK downloads, not using an icon and registering services related to system events is an alarming new strategy.
BleepingComputer contacted Google for comment on whether it plans to introduce any measures to block this tactic, and a spokesperson sent us the following statement:
Based on our current detections, no apps containing this malware have been found on Google Play.
Android users are automatically protected against known versions of this malware using Google Play Protect, which is turned on by default on Android devices with Google Play Services.
Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play. – Google spokesperson
Update 3/14 – Added Google statement